When your VPS turns out to be sending unwanted 'spam' to one or more recipients, you are likely to receive an 'abuse report' from a one of these recipients (or forwarded by us). These notifications will usually also contain the headers of these mails which can be used to determine the source of the spam.
In the past the 'hacking' of mailboxes was the primary source of abusing e-mail addresses, but with the current popularity of content management systems such as WordPress, Joomla, Drupal and others, this has been replaced by "spamscripts" on the web space. Should you receive a report that spam has been sent from your VPS, it is advised to thoroughly check the disk space of the website on your VPS (if applicable) if there are no unknown malicious files.
Example of code in a spam script: 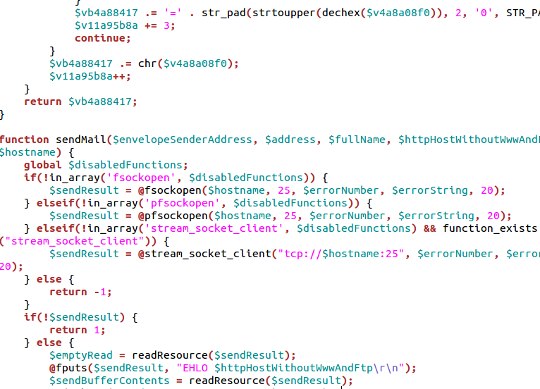
Of course it's difficult to check hundreds or thousands of files used by a CMS to check which files do not belong there. However, spam scripts usually have some common similarities which can be used to recognize it's purpose. After these files will have randomly generated file names (for example 23gw1pnb.php) or look like a legitimate file belonging to a CMS (for example template.config.php). There could also be code embedded in an existing (and legitimate) file. In most cases gzinflate & base64 encoding will be used for masking these scripts.
An example for finding such malicious spam scripts on your VPS is shown below:
find -name "*.php" -exec grep -El '/<?.*eval\(gzinflate\(base64.*' '{}' \;
The output should show all files containing "gzinflate\(base64" from the current directory and below. It's therefore advised to execute this command from the root of your web space. This will however not find every possible spam script. An alternative solution is to check the logs for your mail server, but this will usually only show the source of the mail it self - it's not unheard of that there are other malicious scripts that do not send the spam itself, but replace the spam scripts with new ones once the original spam script is removed.
It's therefore easier and more practical to install a software solution such as ClamAV to scan for these files. A good alternative is Linux Malware Detect (LMD) / Maldet. You can find a guide for installing ClamAV for almost every OS on the ClamAV website. For web control panels the installation of ClamAV differs:
- cPanel has built in support for ClamAV (Go to "Manage Plugins" and select "Configure ClamAV Scanner" to manage it).
- DirectAdmin has no real support, but there is a short guide on it's website: http://help.directadmin.com/item.php?id=370.
- Plesk has no support for ClamAV, but has Dr Web which can perform similar actions. You can find an unofficial guide for using ClamAV with Plesk here.
How can I prevent this from happening?
- Make sure your CMS (and plugins) are always updated to the latest version. For older version vulnerabilities are almost always known!
- Make sure you don't download themes and plugins from unknown websites. It's not uncommon if a "free" download of a normally paid addon is infected with malware.
- Use a plugin such as WordFence to improve the security of your WordPress-website. For Joomla you can look at Securitycheck as a possible addon.
- If you are not using any mail forms on your website: disable PHPmailer. Or disable mailing via port 25 for websites.
- If you do want to use PHP mail forms on your website, make sure the 'TO:' mail address can not be altered directly. Otherwise you enable visitors to start spamming directly from that form.
- For any form of website related abuse it's very important to have the right file permissions set. Almost every framework & CMS has a list of recommended permissions. By using these recommended permission you can prevent vulnerabilities from being used to alter core files of a framework.
- Run a frequent scan with tools such as ClamAV or Linux Malware Detect (LMD) to detect malware on your server as soon as possible. You could plan these scans in a cronjob for example.
- Use our VPS Mailservice so outgoing spam is already filtered / blocked before being sent to the Internet.
- To prevent malicious use of your mail address due to your password being obtained, never use a connection without SSL (in that case your password will be sent in plain text) and always choose a strong password.




