July 1, 2021, Microsoft announced that there is a zero-day vulnerability in the Print Spool Service in Windows (all versions of Windows Server and Windows 10 and older).
The vulnerability in the Print Spooler Service is a remote code execution vulnerability numbered CVE-2021-34527. An attacker who successfully exploits this vulnerability could execute arbitrary code on behalf of the local SYSTEM account.
Update July 7 2021: A patch is now available for the CVE-2021-34527 vulnerability, see the paragraph related to this patch.
The Print Spool Service is only used for remote printing. Because no printers can be connected to VPSs at TransIP, we recommend, as a precaution, to disable the Print Spooler Service on all your Windows Servers. We explain how you can do that in this tutorial.
- If you're using a Domain Controller (DC) AND a Print Server (most likely a local Print Server) which are both connected to the same Windows domain, you actually will need the Print Spool Service on both the DC and Print Server. In that case install the latest security updates instead of disabling the Print Spool Service.
- The steps in this tutorial work for both Windows Servers and desktop computers running Windows 10 (or most older versions).
Step 1
On your Windows Server click on the Windows Start button and type 'services'. In the results, click on 'Services'.
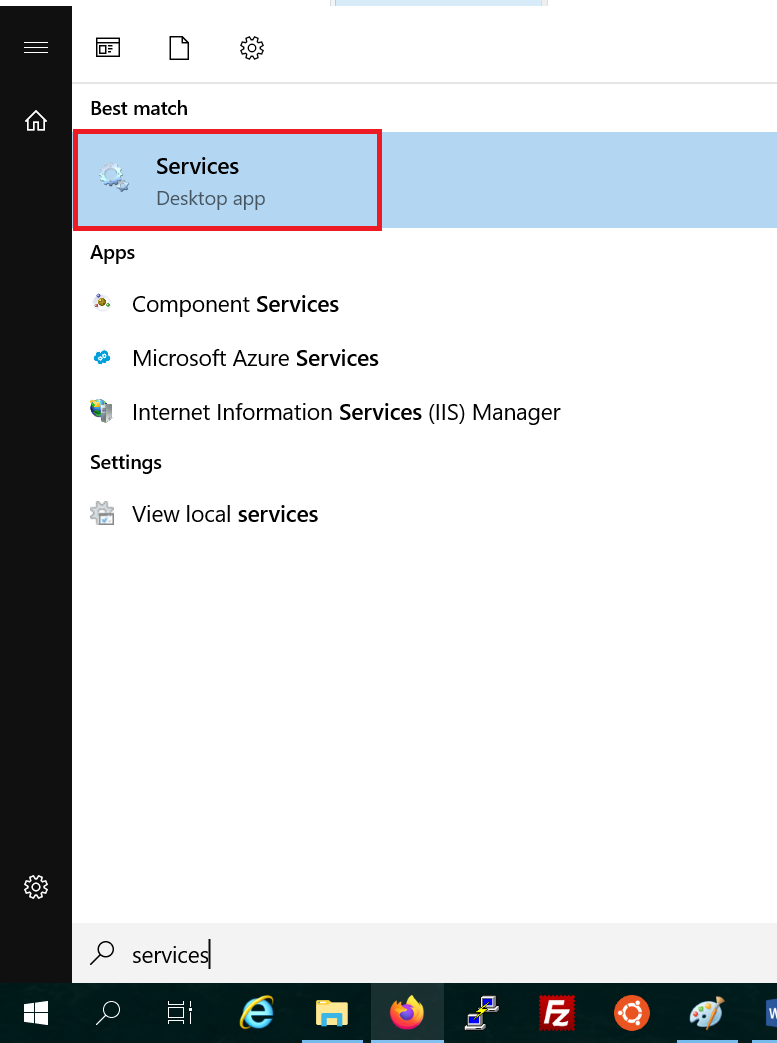
Alternatively, press the Windows flag + R simultaneously on your keyboard and type 'services.msc' in the Window that appears.
Step 2
Scroll down in the 'Services' window and double click with the left mouse button on 'Print Spooler'.
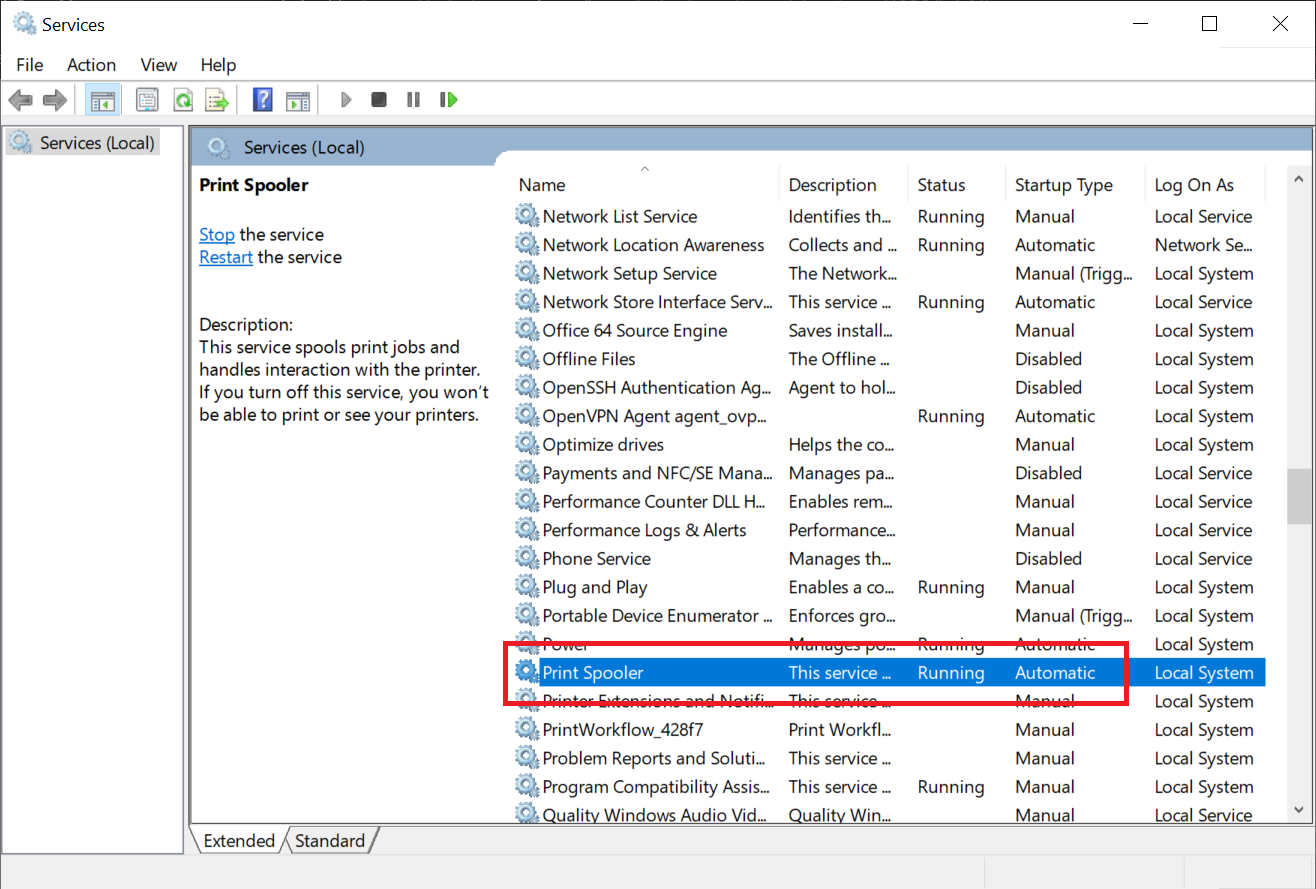
Stap 3
Switch the 'Startup type' to 'Disabled' and click in sequence on 'Stop' > 'Apply' > 'OK'.
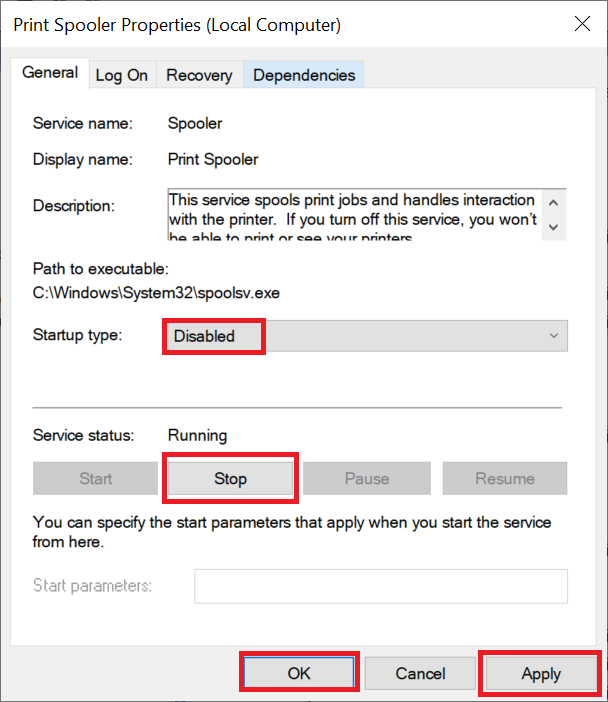
The Print Spooler Service is now disabled on your Windows Server and you are no longer vulnerable to the vulnerability mentioned in this article.
Patches for CVE-2021-34527
July 7th 2021 Microsoft published patches for CVE-2021-34527. The patches work against remote attacks. Even with the patch, it's still possible to perform a local privilege escalation (i.e. obtain more security permissions than the used account actually has). In order to prevent this, users can disable Point & Print functionality using the Group Policy Management Console.
Please note: In Windows Server 2016, 2019 and Windows 10 & 11 Point & Print is not automatically configured. If you haven't configured Point & Print than these Windows (Server) versions only require the installation of this security patch.
As you cannot connect a printer to a VPS, we still recommend disabling the Print Spool Service as it's an easy solution.
The security patch is installed using Windows Updates. Are you behind on your Windows updates? Then, it's important to first install those. In this tutorial we explain how you can manually or automatically install Windows updates.
Should you have any questions left regarding this article, do not hesitate to contact our support department. You can reach them via the ‘Contact Us’ button at the bottom of this page.
If you want to discuss this article with other users, please leave a message under 'Comments'.