Unfortunately there are a lot of active botnets on the Internet, which are constantly scanning IP-ranges to see if they get a hit on port 22 (SSH) and in some cases port 21 (FTP) as well. Because this is done by a very large amount of IP-addresses we can't block or ban all of these from our network.
Furthermore, a lot of infected IP users don't even know they are infected and performing these attacks. Because of that, a block of their IP on our side could cause for a lot of problems when trying to reach a legitimate website in our network. This is something we like to prevent.
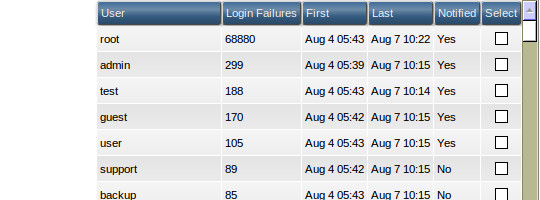 (Example of a brute-force monitor from a DirectAdmin installation)
(Example of a brute-force monitor from a DirectAdmin installation)
What actions can I take to prevent these attacks?
-
Change the SSH-port from port 22 to something else:
When you use the console in the control panel or a SSH connection to log into your server, you can use your favorite editor (like vi or nano) to open and edit the file /etc/ssh/sshd_config. In all of our pre-installed images and when you are using an installation of openSSH yourself, this will be the configuration file for your SSH-server. Be default most lines will be "commented" so the default settings will be used. When you remove the # in the line stating "#Port 22" and change 22 to a different port number, you can use this new port to set up SSH-connections through that port.
Please note that you should not set a port that's already being used by another common protocol! Save the changes and restart sshd or the OS / VPS to make the changes active. If you selected a 'high' portnumber like 12345 for example, you will be required to open this port in the firewall first. Please do so before restarting SSH or the server.
You can also change the port for your FTP-server (even though attacks are a lot less frequent on port 21), but it's depending on the FTP-server you are using in which file the configuration is found. For PureFTPd this is /etc/pure-ftpd.conf, for vsFTPd this is/etc/vsftpd.conf.
-
Install bruteforce protection software:
You can consider using Fail2Ban or SSHguard to stop brute-force attack and block the offending IP's. A 'downside' of using either of these 2 applications is the fact that they currently only work with iptables as a firewall. Most of the new Linux-based OS's have switched to firewalld in their new releases and both programs can't use this. You can always enable / install iptables on your VPS, however if you use the latest pre-installed images of DirectAdmin, cPanel or Plesk (in combination with CentOS 7.1) this could have negative consequences for the operation of your server .




